目次
From OTRS 2.0 on, Access Control Lists (ACLs) can be used to control access to tickets, modules, queues, etc., or to influence actions on tickets (closing, moving, etc.) in certain situations. ACLs can be used to supplement the existing permission system of roles and groups. Using ACLs, rudimentary work-flows within the system can be mapped, based on ticket attributes.
In a general way ACLs are used to reduce the possible options for a ticket based on a defined set of rules.
ACLs can be directly entered into the Kernel/Config.pm
file. whoever this is not any more recommended as OTRS comes now with a GUI
Access Control Lists in the Admin
panel that allows to save the ACLs in the Database as the first step and
then deploy them into a file when they are ready.
This chapter has some ACL examples which will walk you trough the process of defining ACL definitions, and a reference of all possible important ACL settings.
警告
The default user 'root@localhost' is not affeced by the Ticket ACls
The ACL definition can be split into two big parts, 'Matching' and 'Change'. In the matching sections the ACLs contains attributes that has to be met in order to use the ACL, if the attributes defined in the ACL does not match with the attributes that are sent, then the ACL does not take any affect, but any other match ACL will. The change sections contains the rules to reduce the possible options for a ticket.
Matching Sections
項目
This section contains matching options that can be changed on the fly, for example on a ticket creation time the data of the ticket changes dynamically as the agent sets the information, if an ACL is set to match a ticket attribute then only when the matching attribute is selected the ACL will be active and might reduce other ticket attributes, but as soon as another value is selected the ACL will not take any affect.
PropertiesDatabase
This section is similar to 'Properties' but does not take changes in ticket attributes that are not saved into the DataBase, this means that changing an attribute without submit will not make any affect. This section is not use for ticket creation screens (as tickets are not yet created in the Database).
Change Sections
Possible
Possible section resets the data to be reduce to only the elements that are set in this section.
PossibleAdd
Elements in PossibleAdd section add missing elements that where reduced in other ACLs. PossibleAdd is only used in together with other ACLs that have Possible or PossibleNot sections.
PossibleNot
This section is used to remove specific elements from the current data. It could be used stand alone or together with other ACLs with a Possible or PossibleAdd sections.
In order to make the development of ACLs easier and more powerful there is a set of so called modifiers for the attributes on each section. This modifiers as explained below:
Modifiers
[Not]
This modifier is used to negate a value for example: '[Not]2 low' in this case talking about ticket priorities will be the same as to have: '1 very low', '3 normal', '4 high', '5 very high'.
[RegExp]
It is use to define a regular expression for matching several values, for example '[RegExp]low' talking about priorities is the same as '1 very low', '2 low'.
[regexp]
It is very similar to [RegExp] but it is case insensitive.
[NotRegExp]
Negated regular expressions for example '[NotRegExp]low' talking about priorities is the same as '3 normal', '4 high', '5 very high.
[Notregexp]
It is very similar to [NotRegExp] but it is case insensitive.
The following examples are shown in both ways graphical and text based.
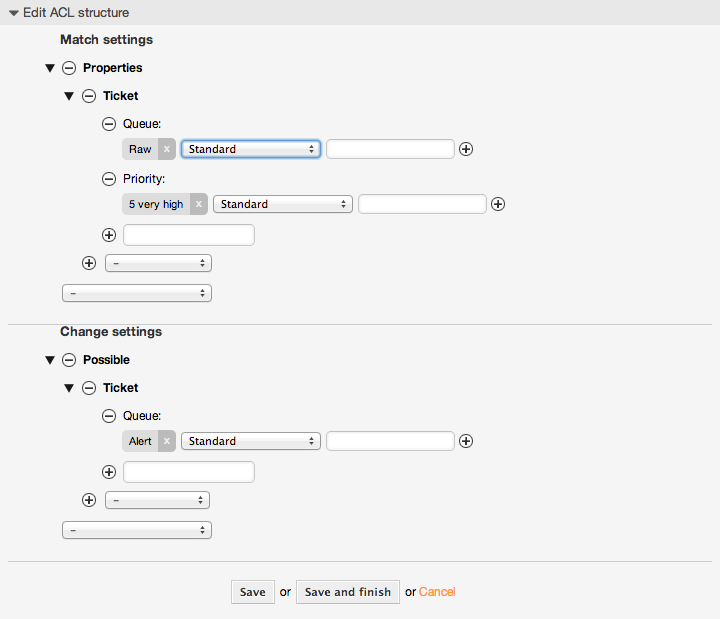
例5.1 ACLはチケット優先度5のチケットのみをキューへの移動を許可します。
This example shows you the basic structure of an ACL. First, it needs to have a name. In this case, it is "ACL-Name-2". Note that the ACLs will be numerically sorted before execution, so you should use the names carefully.
Secondly, you have a "Properties" section which is a filter for your tickets. All the criteria defined here will be applied to a ticket to determine if the ACL must be applied or not. In our example, a ticket will match if it is in the queue "Raw" and has priority "5 very high". This is also affected by changes in the form (e.g. if the ticket is the queue "raw" and had a priority "3 normal" at this moment the ACL will not match, but then priority drop-down is selected and the priority is changed now to "5 very high" then will also match).
最後に、「可能」セクションは画面への修正を定義します。この場合、利用可能キューから、「警告」キューだけがチケット・画面の中で選択することができます。
# ticket acl
$Self->{TicketAcl}->{'100-Example-ACL'} = {
# match properties
Properties => {
# current ticket match properties
Ticket => {
Queue => ['Raw'],
Priority => ['5 very high'],
}
},
# return possible options (white list)
Possible => {
# possible ticket options (white list)
Ticket => {
Queue => ['Alert'],
},
},
};
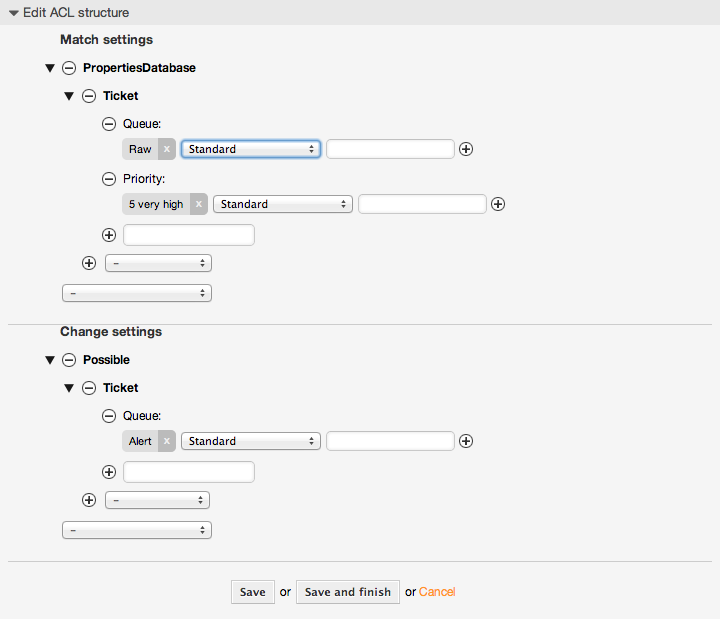
例5.2 データベースに格納された優先度5のチケットだけのキューへ移動を許可するACL
この例は先のものに非常に似ています。しかしながら、この例では、「生で」かつ優先度が「5:非常に高い」チケットのみが両者ともにデータベースに保存されて、マッチします。チケットがデータベースの中で実際に更新される前に、この種のACLはフォームの変更を考慮しません。
# ticket acl
$Self->{TicketAcl}->{'102-Example-ACL'} = {
# match properties
PropertiesDatabase => {
# current ticket match properties
Ticket => {
Queue => ['Raw'],
Priority => ['5 very high'],
}
},
# return possible options (white list)
Possible => {
# possible ticket options (white list)
Ticket => {
Queue => ['Alert'],
},
},
};
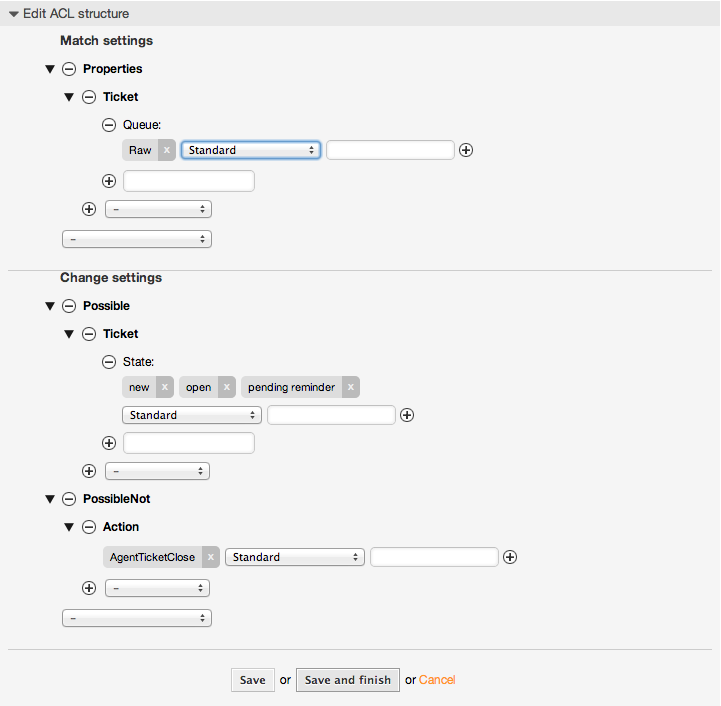
例5.3 未対応のキュー中のチケットの完了を不能にし、閉じるボタンを隠すACL
この例では、どのようにチケット・フィールド(の状態)が、(フォームを選択する1つ以上の可能な値で)フィルターされるかを理解できるでしょう。あるチケット用に実行することができる アクションを制限することも可能です。この場合、チケットは完了できません。
$Self->{TicketAcl}->{'102-Second-Example-ACL'} = {
# match properties
Properties => {
# current ticket match properties
Ticket => {
Queue => ['Raw'],
}
},
# return possible options (white list)
Possible => {
# possible ticket options (white list)
Ticket => {
State => ['new', 'open', 'pending reminder'],
},
},
3 return also not possible options (black list)
PossibleNot => {
# not possible action options
Action => [ 'AgentTicketClose' ],
},
};
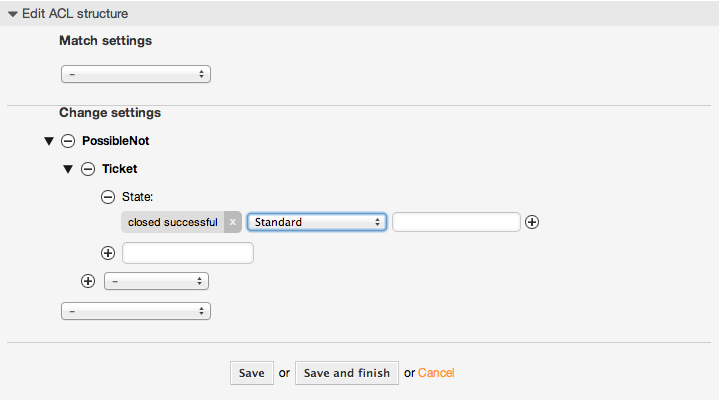
例5.4 状態:「閉鎖成功」を常に削除するACL
ここの例では、否定フィルタ(状態:「完了(成功)」を取り除く)をどのようにして定義可能か例示します。チケット用のマッチ・プロパティを定義しなければ、どんなチケットでもマッチすることもわかります。例えばACLが常に当てはまります。これは、もしデフォルトで特定の値を非表示にしたくかつ、特殊な環境(例えば担当者が特定のグループにいるならば)だけにそれらを可能にしたいなら活用可能になります。
$Self->{TicketAcl}->{'103-Third-ACL-Example'} = {
# match properties
Properties => {
# current ticket match properties (match always)
},
# return possible options
PossibleNot => {
# possible ticket options
Ticket => {
State => ['closed successful'],
},
},
};
例5.5 "HW"で始まるキューが作成されるハードウェア・サービス・チケットのみを表示するACL
ここでは、マッチするチケットと利用可能なオプションのフィルタリングのための正規表現を使用することができるかについても例示します。
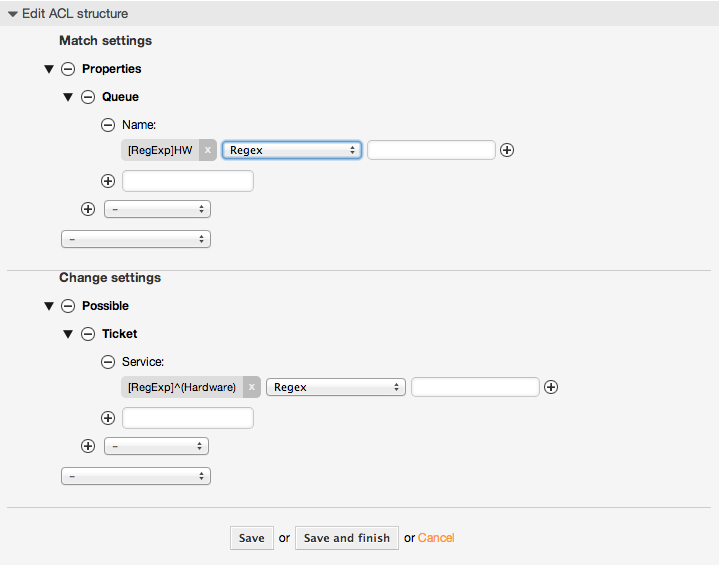
$Self->{TicketAcl}->{'104-Only-Hardware-Services-for-HW-Queues-ACL'} = {
# match properties
# note we don't have "Ticket => {" because there's no ticket yet
Properties => {
Queue => {
Name => ['[RegExp]HW'],
}
},
# return possible options
Possible => {
# possible ticket options
Ticket => {
Service => ['[RegExp]^(Hardware)'],
},
},
};
例5.6 ACL to restrict a Process in the customer frontend using the CustomerID.
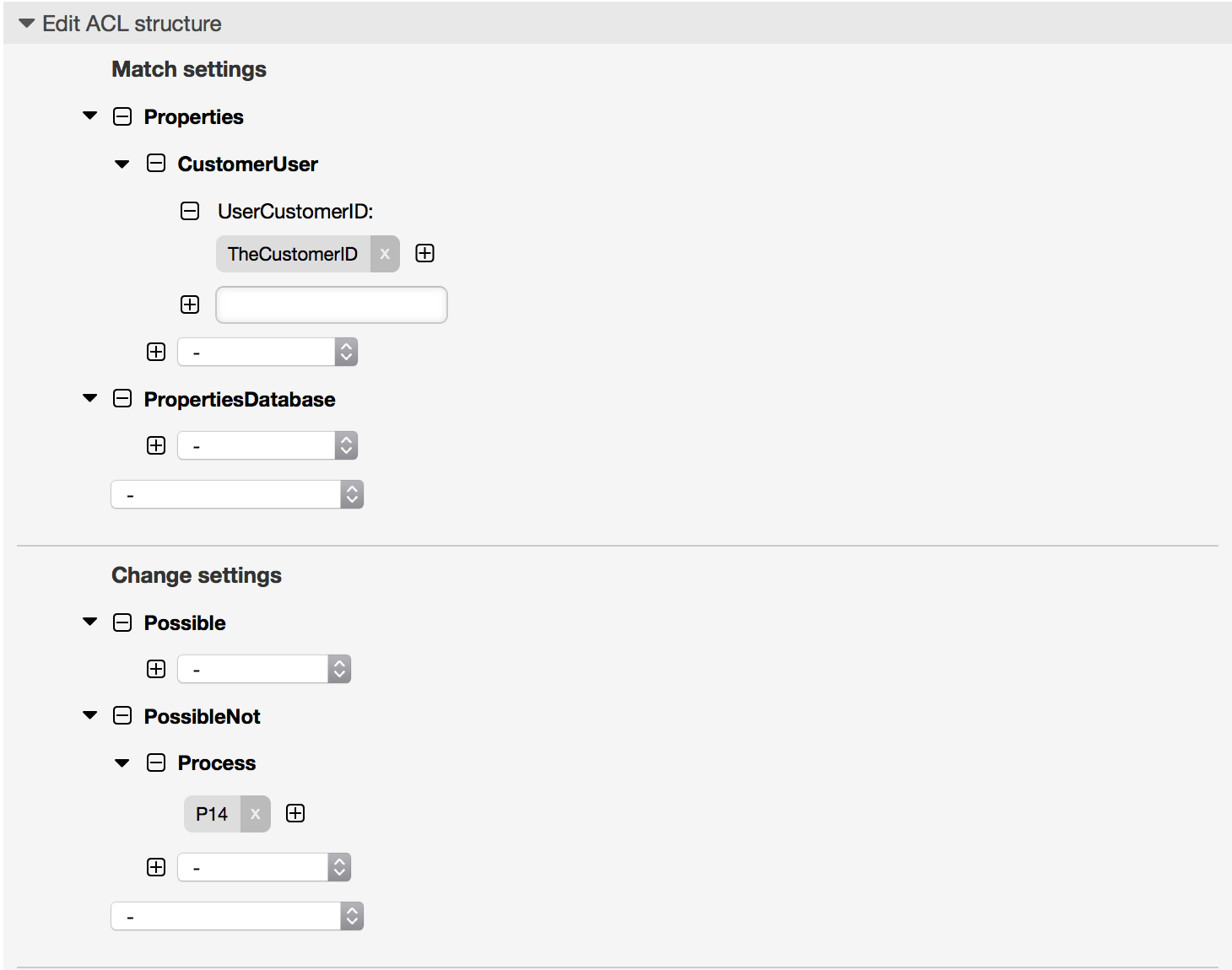
$Self->{TicketAcl}->{"105-Disallow-Process-For-CustomerID"} = {
'Possible' => {},
'PossibleNot' => {
'Process' => [
'P14'
]
},
'Properties' => {
'CustomerUser' => {
'UserCustomerID' => [
'CustomerID'
]
}
},
'PropertiesDatabase' => {},
'StopAfterMatch' => 0
};
下記の例において、ACLで使用可能な全パラメーターのリストがあります。
Please see the section on ACLs in the ProcessManagement documentation for a detailed description of how to use ACLs for process tickets.
例5.7 全ての可能かつ重要なACL設定を示すリファレンス(参照)
# ticket acl
$Self->{TicketAcl}->{'200-ACL-Reference'} = {
# match properties (current values from the form)
Properties => {
# the used frontend module
Frontend => {
Action => ['AgentTicketPhone', 'AgentTicketEmail'],
},
# the logged in agent
User => {
UserLogin => ['some login'],
Group_rw => [
'hotline',
],
Role => [
'admin',
],
# ...
},
# the logged in customer
CustomerUser => {
UserLogin => ['some login'],
UserCustomerID => ['some customer id'],
Group_rw => [
'hotline',
],
Role => [
'admin',
],
# ...
},
# process properties
Process => {
ProcessEntityID => ['Process-9c378d7cc59f0fce4cee7bb9995ee3eb'], # the Process that the current ticket is part of
ActivityEntityID => ['Activity-f8b2fdebe54eeb7b147a5f8e1da5e35c'], # the current Activity of the ticket
ActivityDialogEntityID => ['ActivityDialog-aff0ae05fe6803f38de8fff6cf33b7ce'], # the current ActivityDialog that the Agent/Customer is using
},
# ticket properties
Queue => {
Name => ['Raw'],
QueueID => ['some id'],
GroupID => ['some id'],
Email => ['some email'],
RealName => ['OTRS System'],
# ...
},
Service => {
ServiceID => ['some id'],
Name => ['some name'],
ParentID => ['some id'],
# ...
},
Type => {
ID => ['some id'],
Name => ['some name'],
# ...
},
Priority = {
ID => ['some id'],
Name => ['some name'],
# ...
},
SLA = {
SLAID => ['some id'],
Name => ['some name'],
Calendar => ['some calendar'],
# ...
},
State = {
ID => ['some id'],
Name => ['some name'],
TypeName => ['some state type name'],,
TypeID => ['some state type id'],
# ...
},
Owner => {
UserLogin => ['some login'],
Group_rw => [
'some group',
],
Role => [
'admin',
],
# ...
},
Responsible => {
UserLogin => ['some login'],
Group_rw => [
'some group',
],
Role => [
'admin',
],
# ...
},
DynamicField => {
# Names must be in DynamicField_<field_name> format.
# Values in [ ... ] must always be the untranslated internal data keys
# specified in the dynamic field definition and
# not the data values shown to the user.
DynamicField_Field1 => ['some value'],
DynamicField_OtherField => ['some value'],
DynamicField_TicketFreeText2 => ['some value'],
# ...
},
# alternatively, ticket properties can be specified in the ticket hash
Ticket => {
Queue => ['Raw'],
State => ['new', 'open'],
Priority => ['some priority'],
Lock => ['lock'],
CustomerID => ['some id'],
CustomerUserID => ['some id'],
Owner => ['some owner'],
DynamicField_Field1 => ['some value'],
DynamicField_MyField => ['some value'],
# ...
},
},
# match properties (existing values from the database)
PropertiesDatabase => {
# See section "Properties", the same config can be used here.
# ...
}
# reset possible options (white list)
Possible => {
# possible ticket options (white list)
Ticket => {
Queue => ['Hotline', 'Coordination'],
State => ['some state'],
Priority => ['5 very high'],
DynamicField_Field1 => ['some value'],
DynamicField_MyField => ['some value'],
# ...
NewOwner => ['some owner'],
OldOwner => ['some owner'],
# ...
},
# Limit the number of possible ActivityDialogs the Agent/Customer
# can use in a process ticket.
ActivityDialog => ['AD1', 'AD3'],
# Limit the number of possible Processes that can be started
Process => ['Process-9c378d7cc59f0fce4cee7bb9995ee3eb', 'Process-12345678901234567890123456789012'],
# possible action options (white list)
Action => [
'AgentTicketBounce',
'AgentTicketPhone'. # only used to show/hide the Split action
'AgentLinkObject', # only used to show/hide the Link action
# ...
],
},
# add options (white list)
PossibleAdd => {
# See section "Possible"
# ...
},
# remove options (black list)
PossibleNot => {
# See section "Possible"
# ...
},
};
注記
ACLとマッチしている間に、CustomerUserIDパラメーターが送られると、ACLメカニズムは、CustomerUserハッシュを満たすCustomerUser詳細を集めるために、供給されたCustomerUserIDを使用して、定義されたACLを比較します。またそれは、プロパティ(特性)・マッチ用のチケット・ハッシュ中の顧客情報を無効に(override)します。この計算もPropertiesDatabase部分のためになされるが、その一方で、データを集めるために基礎としてチケット・顧客(the Ticket Customer)を使用しています。
顧客・インターフェースでは、CustomerUserIDが現在の記録された顧客ユーザとともに常に送信されることに注目してください。
Be aware that in ticket search screens (AgentTicketSearch and CustomerTicketSearch) the only affected attributes by ACLs are the Dynamic Fields. This means that this screens you can not restrict any other attribute like ticket type, state, queue, etc.
From OTRS 4 the 'Action' parameter is not longer a hash but an array reference and it can be used in any of the Change sections using any of the Modifiers.